Description: Stored XSS vulnerability in Vtiger Open Source Edition
Version affected: Vtiger Open Source Edition <= v8.3.0
Version fixed: N/A
System: https://www.vtiger.com/open-source-crm/
Researcher: Simon Njuguna
Description:
A Stored Cross-Site Scripting (XSS) vulnerability exists in Vtiger CRM Open Source Edition v8.3.0, exploitable via the "Services" import feature. An attacker can craft a malicious CSV file containing an XSS payload in the "Service Name" field. When the file is uploaded, the application improperly sanitizes user input, leading to persistent script execution.
Any authenticated user, including an administrator, who views the imported service record triggers the malicious payload. This allows attackers to execute arbitrary JavaScript in the victim's browser.
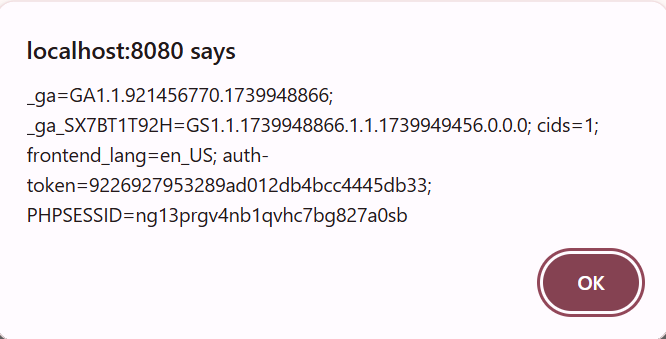
Additionally, Vtiger CRM does not set the HttpOnly flag on authentication cookies, making them accessible to client-side scripts. This enables attackers to steal session tokens and hijack administrator accounts, potentially compromising the entire application.
Impact:
- Stored XSS execution on all users interacting with imported service records.
- Possible session hijacking of administrative users due to exposed authentication cookies.
Steps to reproduce the vulnerability
Create a CSV file with the following payload
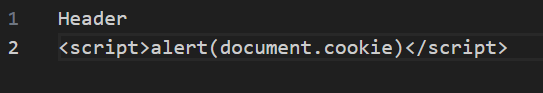
Login to vtiger and navigate to Inventory > Services and click Import
Select the csv file and click next
In the field mapping section, under CRM fields, select Services Name * and click import.
The xss payload will appear under the service name:
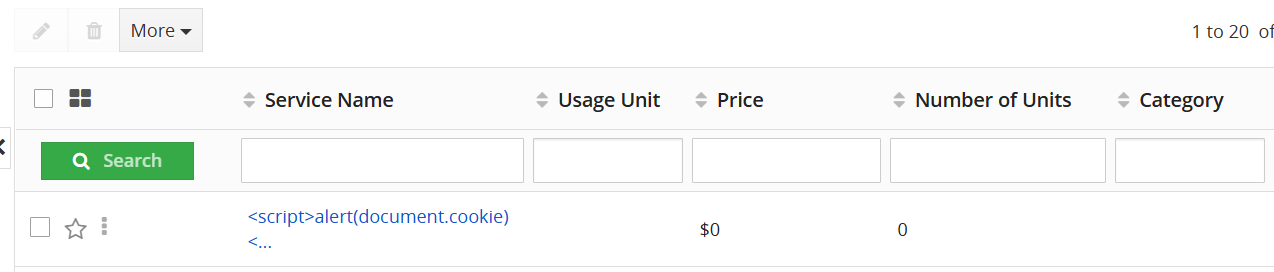
Click the service name to trigger the xss and capture the session ID: