Description: Stored XSS vulnerability in SeedDMS
Version affected: SeedDMS - v6.0.32
Version fixed: SeedDMS - v6.0.33
System: https://sourceforge.net/projects/seeddms/files/seeddms-6.0.32/
Researcher: Simon Njuguna
Proof of concept
Description: A stored cross-site scripting (XSS) vulnerability exists in SeedDMS
6.0.32. This vulnerability allows an attacker to inject malicious
JavaScript payloads by creating a folder/document with an XSS payload as the document name add adding the folder/document to the clipboard.
Steps to reproduce the vulnerability
Create a folder with the name <script>alert(0)</script>
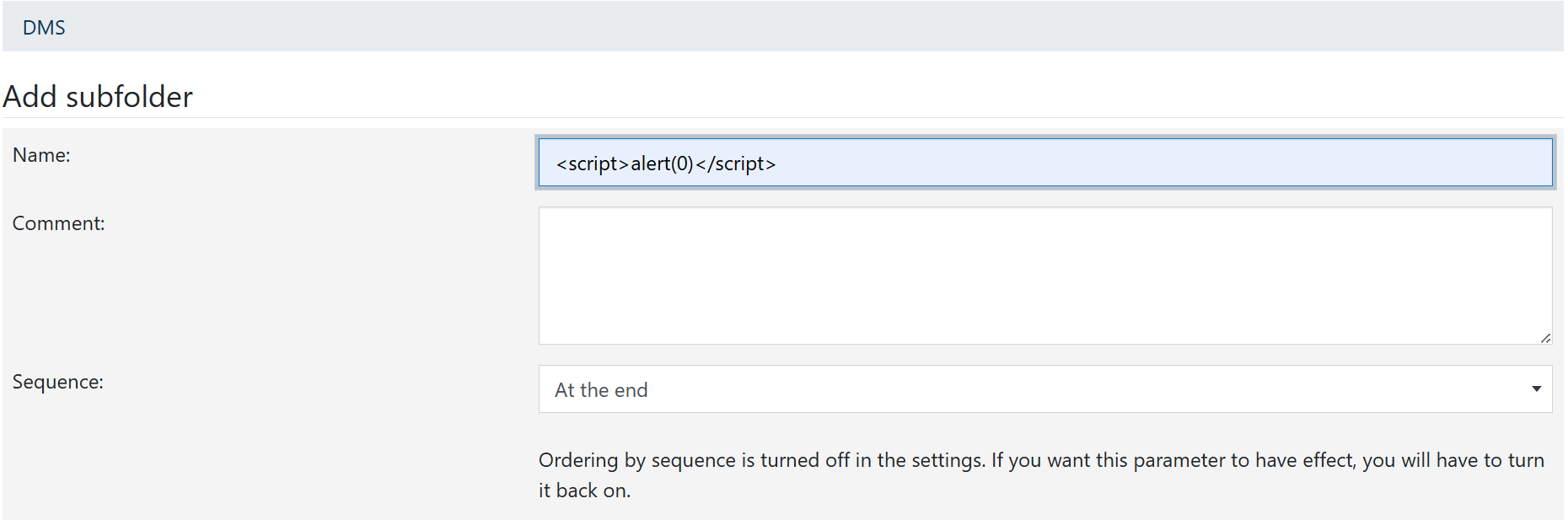
Drag the folder and drop it in the clipboard
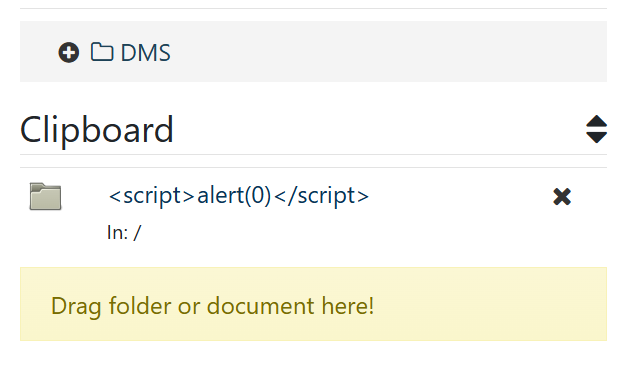
Click the folder name or refresh the page


