Description: Authenticated RCE vulnerability in SeedDMS
Version affected: SeedDMS <= v6.0.32
Version fixed: N/A
Solution: Set enableExtensionImport="false"
System: https://sourceforge.net/projects/seeddms/files/seeddms-6.0.32/
Researcher: Simon Njuguna
PoC: https://github.com/cyspa/CVEs/blob/main/CVE-2025-45752
Description: A vulnerability in SeedDMS 6.0.32 allows a privileged attacker to execute arbitrary PHP code by exploiting the zip import functionality in the Extension Manager
The attacker could potentially gain remote access to the hosting
server by including a reverse shell payload in the conf.php file in the
extensions zipped file. The reverse shell payload executes after browsing to the zip file clicking the import extension button
Steps to reproduce the vulnerability
- Open a netcat listener
nc -lnvp 4444
- Open a seeddms module zip file. In the module's config.php file, append a reverse shell payload
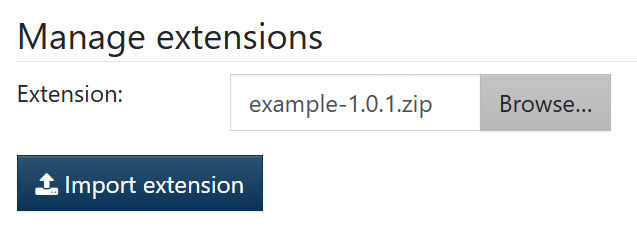
- upload the zip file by navigating to Admin tools > Manage Extensions
- Click browse and select the zip file
- click import extension
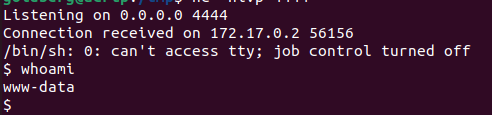
- A connection will be received on the listener
Solution
In settings.xml, you can disable the extensions import feature:
<extensionmgr enableExtensionDownload="true" enableExtensionImport="false" enableExtensionImportFromRepository="true"/>

